Find out how to setup single sign-on with Microsoft/Azure AD
This guide will walk you through how to setup Single Sign-On between Expiration Reminder and Microsoft Entra (formerly Azure AD).
Setting up Microsoft Entra/Azure AD
To configure Microsoft Entra/Azure Active Directory, first add the Expiration Reminder app into your account. For this, go to your Microsoft 365 admin center and click on Microsoft Entra/Azure Active Directory from the left menu.
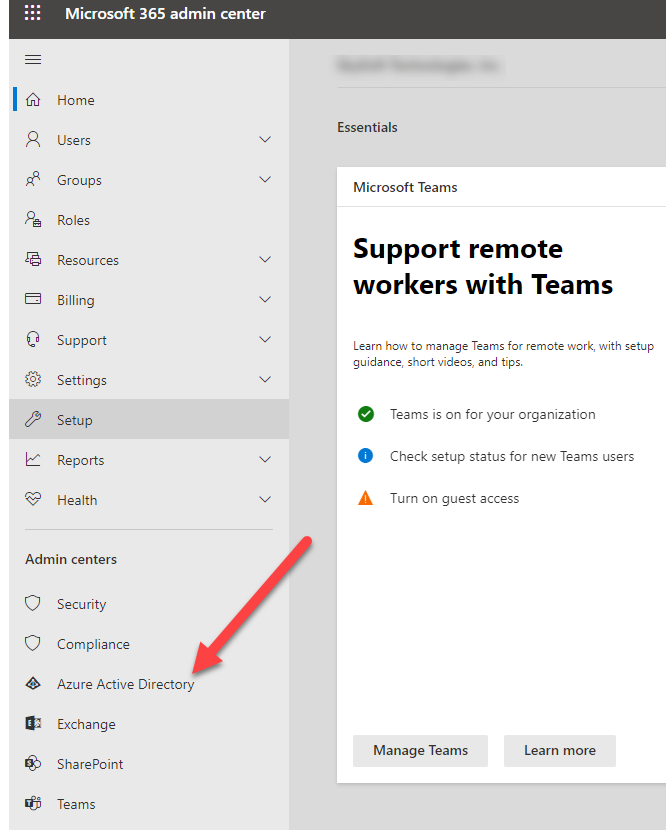
This will take you to Microsoft Entra/Active Directory. From the left menu, click on Enterprise applications.
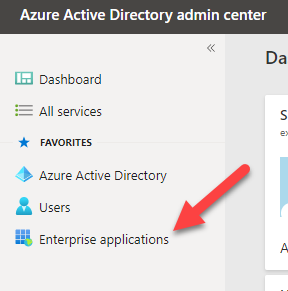
Then click on New Application.
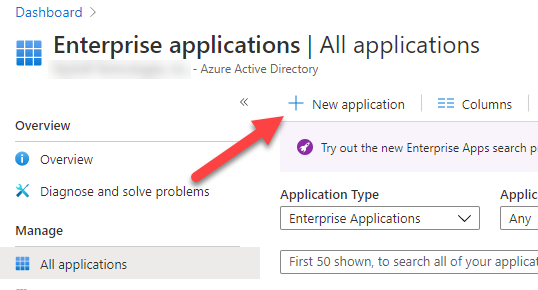
Look for the Expiration Reminder app.
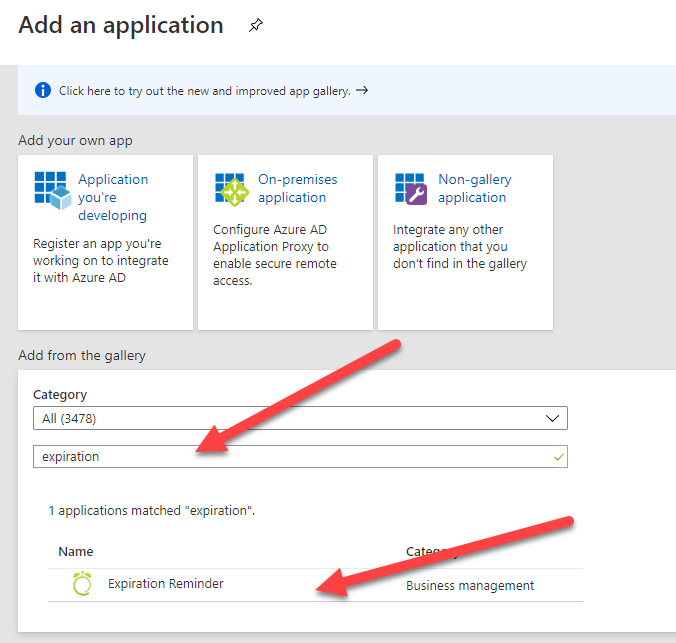
Add the app to your account. The app will be provisioned. Then click on Single Sign-On from the left menu.
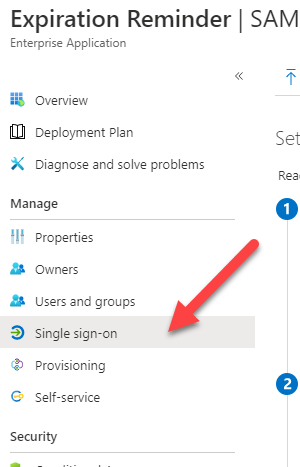
Then select SAML as the provider.
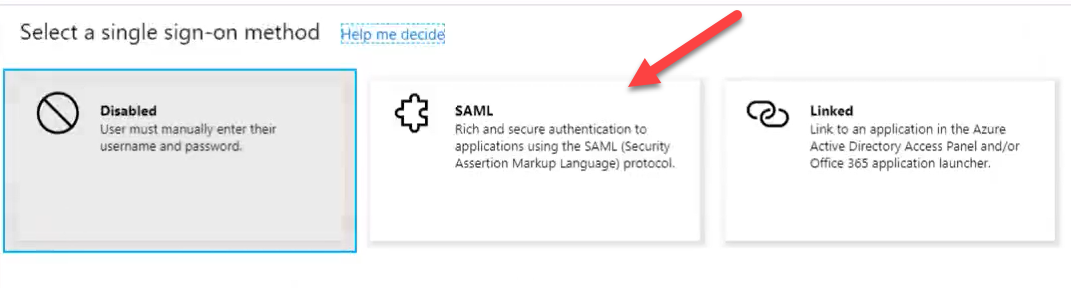
Click on the little pencil on Basic SAML configuration:
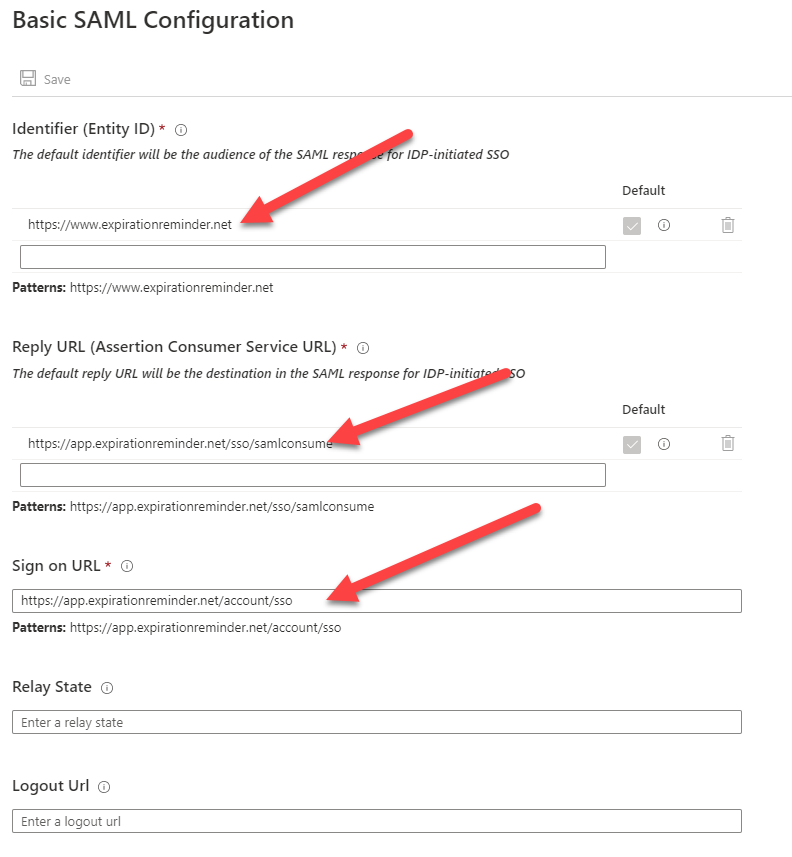
Enter the configuration as shown below.
Proceed now to add users that can use the Expiration Reminder app to login. To do this, click on Users and groups from the left menu.
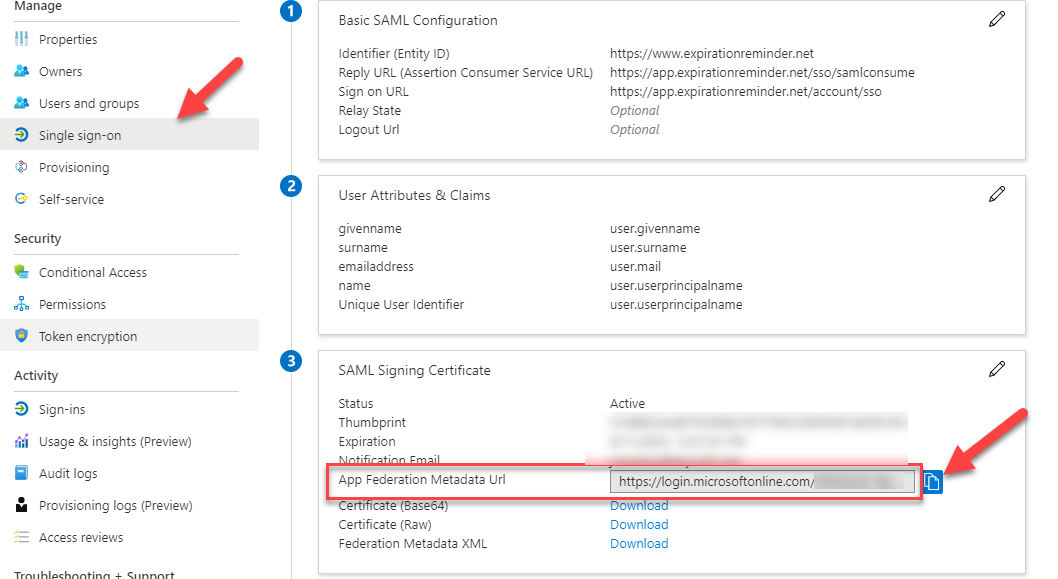
Now, from the Single Sign-On page, copy the App Federation Metadata Url. You'll need this for Expiration Reminder.
Configuring SSO in Expiration Reminder
To configure SSO in your Expiration Reminder account, on the top menu click on Your Name in the top-right corner, then on Settings from the drop-down menu.
Then click on Features on the left menu.
Then click on Configure SSO/SAML.
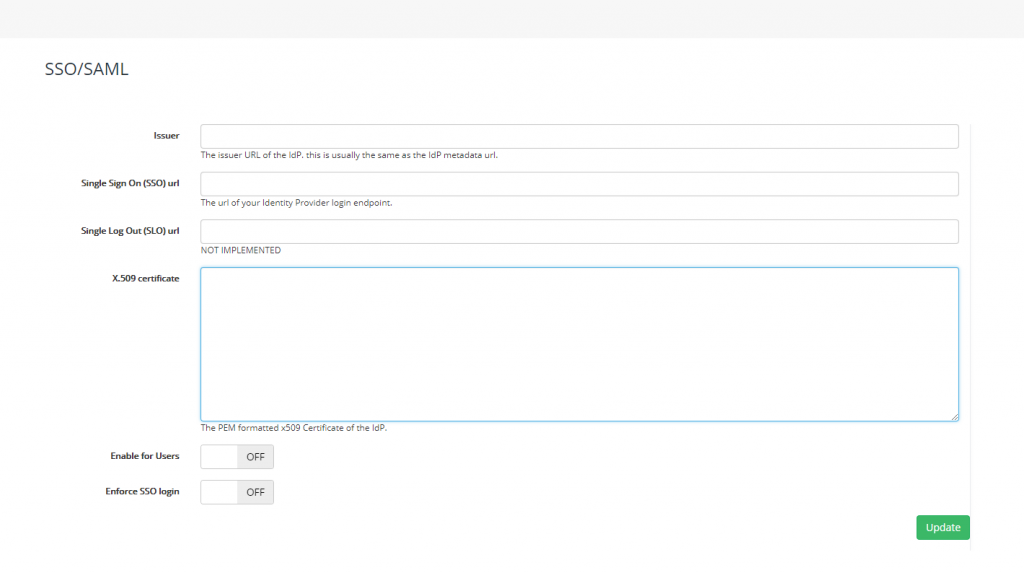
In the SSO screen configure the following fields:
-
Issuer: this is usually the App Federation Metadata Url provided by your directory provider. If possible, Expiration Reminder will try to get the sign on url, the sign out url and the certificate automatically from this metadata url. For Azure AD, this the url you just copied.
-
Single Sign On (SSO) url: this is the url users will be redirected to for login in.
-
Single Log Out (SLO) url: this is the url provided by your Identity Provider for signing out.
-
X.509 certificate: this is the certificate provided by your Identity Provider to authenticate the login request.
-
Enable for Users: This will allow users in Expiration Reminder to be able to use SSO to login to the application. They’ll still be able to use their own Expiration Reminder password if they’d like to.
-
Enforce SSO login: This option will prevent users from using their Expiration Reminder password to login and will force them to use the credentials from the Identity Provider.
Click Update to save your settings.
For setting up the SSO on Microsoft Entra/Azure AD using Expiration Reminder's information:
The ACS URL is: https://app.expirationreminder.net/sso/metadata
The Entity ID is: https://www.expirationreminder.net/

